
Cloud security is a collection of procedures and technology designed to address external and internal threats to business security. Organizations need cloud security as they move toward their digital transformation strategy and incorporate cloud-based tools and services as part of their infrastructure.
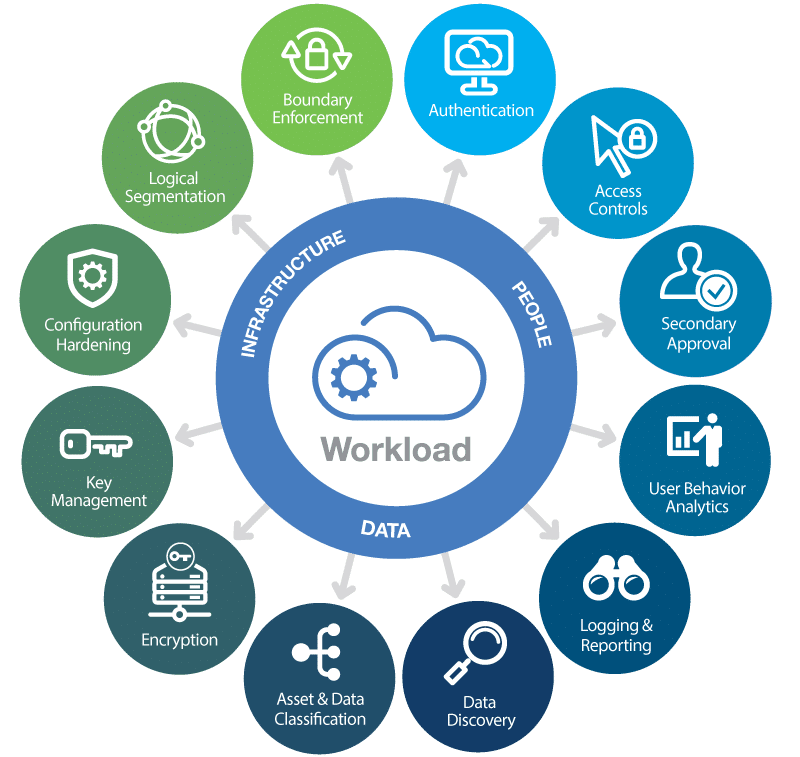
In modern-day enterprises, there has been a growing transition to cloud-based environments and IaaS, Paas or SaaS computing models. The dynamic nature of infrastructure management, especially in scaling applications and services, can bring a number of challenges to enterprises when adequately resourcing their departments. These as-a-service models give organizations the ability to offload many of the time-consuming, IT-related tasks.
Monitoring who accesses data in cloud environments, especially outside corporate networks, is difficult.
Public cloud environments hosting multiple clients can expose services to risks from attacks on other businesses.
Controlling access to cloud systems is harder than on-premises, especially without BYOD policies.
Compliance with data regulations can be confusing in hybrid clouds, even with third-party tools.
Expert support is available to implement custom security measures and standards.
Misconfigured assets, such as default passwords, are a common cause of security breaches in cloud environments.
Our experts can provide any information you need and help you choose the perfect plan for your needs.