
Ideal for small websites and startups
Perfect for growing businesses
Best for large-scale enterprises
A web application firewall (WAF) protects web applications by monitoring HTTP traffic between a web application and the Internet. WAF usually protects web applications against attacks such as cross-site spoofing, cross-site scripting, XSS, file inclusion and SQL injection, etc.
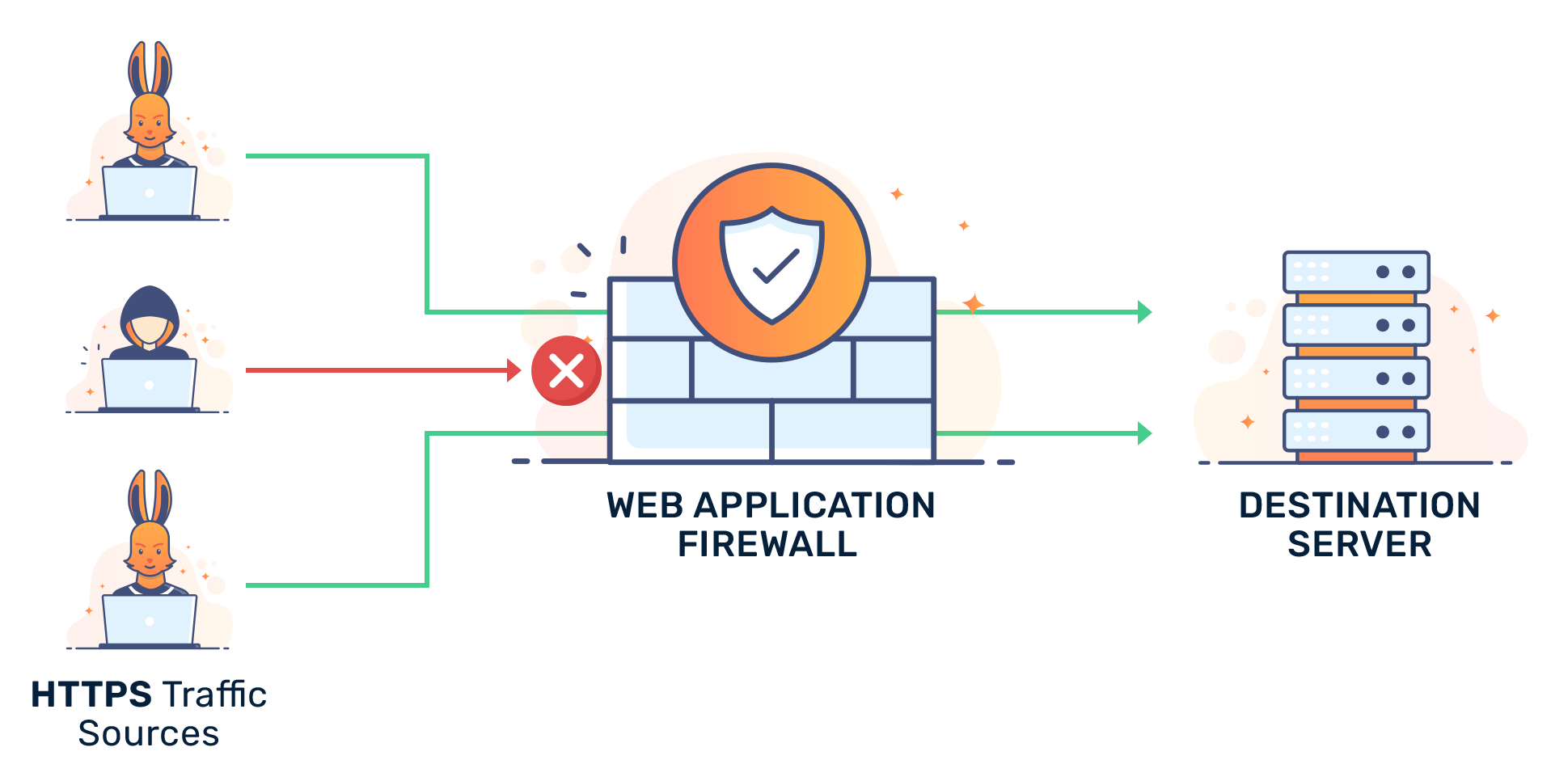
WAF is a layer 7 defense in the OSI model. Organizations typically store sensitive data in back-end databases accessed by web applications. Many business interactions occur via mobile and web applications at this layer, where users interact with the system.
Our experts can provide any information you need and help you choose the perfect plan for your needs.